Gmail, Yahoo!, AOL and More Now Require DKIM. And That Might Be a Problem.
Since the start of 2024, the amount of phishing has been rising and anyone who uses email is a potentially a victim. Has this increase in phishing been fueled by upcoming requirements for two email validation methods? Verifying sender IP addresses and cryptographic authentication.
Let's dig into this theory.
Any business that sends and receives email will have to configure and enable these validation settings if they want to send email messages to the largest email hosts on the planet. If these configurations are not enabled, email messages will “bounce” off the receiving email server and never get delivered.
Furthermore, it also means that any remaining email servers that do not enable these validation methods will be inundated by spam. When the authentication is enforced, criminal organizations, that are responsible for much of the exploitive spam messages, will no longer be able to rely on their old methods on the compliant email servers. When that happens they will turn their attention to the non-compliant.

Since late January, early February, you may have had trouble sending email to Yahoo!, AOL, AT&T email addresses. If you did have this problem, you might have received this message: "When Office 365 tried to send your message, the receiving email server outside Office 365 reported an error."
That’s because those domains started implementing the authentication requirements. This month, Gmail will be fully implementing these requirements for all senders as well.
Businesses that use Microsoft O365 email have been hit especially hard, due to a configuration issue that only Microsoft could resolve (and took some time to find a fix). This "bounce" is what the spammers will experience, and they don’t like it.
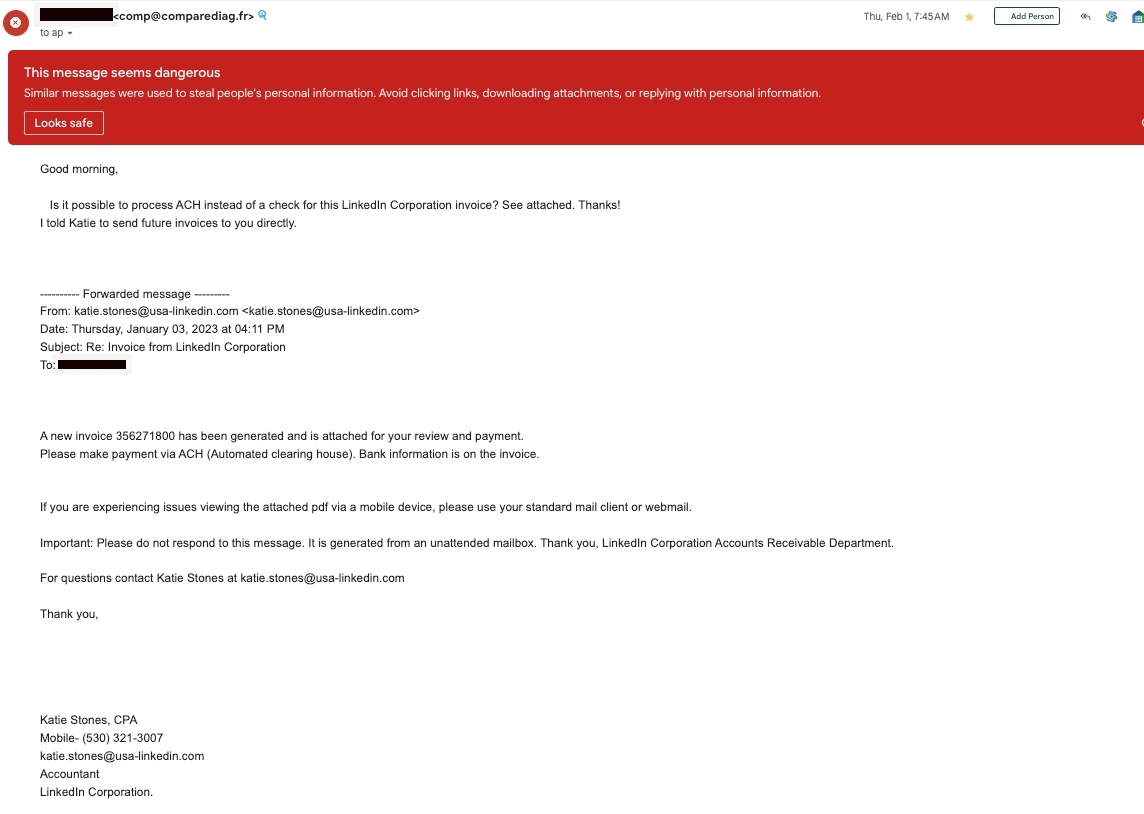
Since the start of the new year and before the requirements kick in, spammers have been hard at work trying to pump as many spammy and scammy emails out as they can. We’ve seen a big increase in the number of fraudulent emails that are sent to accounting teams, even our own. These messages may look like they’ve been sent by an employee (current or former) asking to have their direct deposit account changed. Or there may be a message from the owner asking the accounting team to ACH or wire funds to an account immediately.
They are all fake and these messages come from email addresses that are bizarre.


The Covid pandemic has spurred the rise of techno-terrorism, which has only continued to escalate. The most concerning form of this techno-terrorism has been ransomware.
Ransomware criminal organizations have cost large and small businesses worldwide hundreds of millions of dollars. They have taken down some of the nation's critical infrastructure. They have even crippled Las Vegas casinos.
Hollywood would like you to think that lone hackers in dark rooms are penetrating the network defenses of corporations. Then using sophisticated software, the hacker breaks into each machine, slowly but surely taking down the business.
However, this just isn’t the case. The number one-way ransomware is able to enter a business is not though hacking the security infrastructure. The truth is, over 90% of ransomware attacks start from an employee opening a phishing email.

Some of the perpetrators are criminal groups that have grown so large that they now “license” their ransomware apps to ransomware "affiliates". The “affiliates” "affiliate" shares a cut of any ransom they collect with the criminal groups.
To add fuel to the fire, AI, like ChatGPT, has given criminal groups new tools to create very realistic phishing messages (now with proper grammar!. These AT generated phishing emails are hard for spam filters to detect. At first glance, they are even hard for even a trained eye to detect.
Once there was enough pain, the collective internet finally decided to make the email registrations mandatory.
Take your time and read any message that is asking you to take some sort of immediate financial action. Use a skeptical eye when reading these messages. Most of these messages will be caught by spam detection, but some of the more sophisticated spammers can find ways to get one past the goalie.
Don’t be too concerned if you do see a suspicious email in your account. These criminals are having their last gasp of air before the new regulations shut off their oxygen. And, no, you haven’t been “hacked”. Receiving a fraudulent spam email purporting to be from an employee of the company in your inbox means the spammer is good at their job...and desperate, for now.
Read more information on the DMARC regulation and what to expect at: DMARK and EMAIL Deliverability









